Understanding when to use OIM Client or OIM Platform is crucial when developing custom code for Oracle Identity Governance (OIG).
This article sheds light on this pivotal decision, guiding you through the optimal usage of these components in various OIG custom code scenarios, such as:
- Event Handlers, Scheduled Tasks, Process Task Adapters, Pre-Populate Plugins, Request Data Validator Plugins, Custom Utilities, Backed MBean, and more.
All the above-mentioned components are utilized in order to create any custom flows in OIG platform in order to enable a robust IAM solution for your enterprise. In these components, we do use multiple OIG JAVA APIs as per the requirement of flows, but depending upon the type of component you are using, the instantiation of OIG JAVA APIs can be different in respective components.
Refer to the details below for specifics on instantiating the APIs in each component.
Pre-Requisites
Ensure your OIG Platform is either version 11g or 12c.
Usage of OIM Client v/s OIM Platform
There are multiple components in OIG which require custom code to be written in Core Java so that we can suffice the required objective in order to enable the robust IAM flow for your enterprise.
The various lets of component in OIG for which we must write the Java Code and use the OIG Java APIs to fetch the data from OIM servers and process the data accordingly are as follows:
| OIG Component Name which requires Development in Core Java and has usage of OIM Java APIs |
| Event Handler |
| Scheduled Task |
| Pre-Populate Plugins |
| Pre-Populate Adapters |
| Request Data Validator Plugins |
| Process Task Adapter |
| Backend MBean for UI Specific Changes |
| Standalone Utility <To perform any crone jobs into OIG at the backend without deploying the component outside OIM Server> |
| Groovy Script (Which are used for Reconciliation and Provisioning transformations for application onboarded through AOB approach). This component is out of scope for OIM 11g versions |
| External UI/Web Application |
Usage of OIM Platform based API Connections
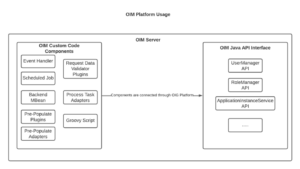
Refer the below block diagram which will give you a high-level understanding on when and for which component we must utilize the OIM Java API connections using OIM Platform.
1) The components of OIM (namely Event Handlers, Scheduled Tasks, Backend MBean, Pre-Populate Plugins, Pre-Populate Adapters, Process task adapter, Groovy scripts, etc,) as mentioned in above block diagram, communicates with OIM using OIM Java APIs. In order to instantiate the OIM Java APIs to extract from OIG or push the data in OIG, you need to use OIM Platform Service for establishing the connection.
2) The sample code is as follows:
| UserManager userManagerAPIInst = null;
userManagerAPIInst = Platform.getService(UserManager.Class); |
3) In the above code block, we have following:
a) UserManager is named OIM API which is used for performing various user specific operations in OIM.
b) userManagerAPIInst is name of object of OIM API Class named as: UserManager
c) In order to instantiate the UserManager API so that we can start the communication with the OIM server, we used OIM Platform Class to do the same.
4) Another way to identify on when to use OIM Platform based connection while instantiating OIM APIs is:
a) When you develop any component which will be deployed inside the OIM server.
b) Refer to the below table for further details:
| Component Name of OIG | Where it is deployed? | Whether to use OIM Platform based connection? |
| Event Handler | Inside OIM Server deployed as Plugin | Yes |
| Scheduled Task | Inside OIM Server deployed as Plugin | Yes |
| Pre-Populate Plugins | Inside OIM Server deployed as Plugin | Yes |
| Pre-Populate Adapters | Inside OIM Server deployed as Jar | Yes |
| Request Data Validator Plugins | Inside OIM Server deployed as Plugin | Yes |
| Process Task Adapter | Inside OIM Server deployed as Jar | Yes |
| Backend MBean for UI Specific Changes | Inside OIM Server as Jar and deployed through Dev Starter Pack War | Yes |
| Groovy Script (Which are used for Reconciliation and Provisioning transformations for application onboarded through AOB approach) | Inside OIM Server deployed as Groovy Script | Yes |
Usage of OIM Client based API Connections
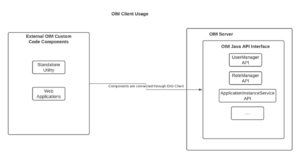
Refer the below block diagram which will give you high level understanding on when and for which component we must utilize the OIM Java API connections using OIM Client:
1) The components of OIM namely Standalone Utility, External UI/Web Application, etc, as mentioned in above block diagram communicates with OIM using OIM Java APIs. In order to instantiate the OIM Java APIs to extract from OIG or push the data in OIG, you need to use OIM Client Service for establishing the connection.
2) The sample code is as follows:
| public class oimClientConnection{
public OIMClient getOIMClientConnectionUtilsMethod(){ OIMClient oimClient = null; /* * Initialization and setting all the system properties */ System.out.println(“****************getOIMClientConnectionUtilsMethod() Method Starts*******************”); //OIMClient oimClient = null; System.setProperty(“java.security.auth.login.config”, “<Auth WL Conf File Location on OIM Server/Other server were you are running the Utility>”); System.setProperty(“OIM.AppServerType”, “wls”); System.setProperty(“APPSERVER_TYPE”, “wls”); Hashtable oimClientEnvironmentVariable = null; oimClientEnvironmentVariable = new Hashtable(); System.out.println(“oimClientEnvironmentVariable : “+oimClientEnvironmentVariable); oimClientEnvironmentVariable.put(OIMClient.JAVA_NAMING_FACTORY_INITIAL, “weblogic.jndi.WLInitialContextFactory”); oimClientEnvironmentVariable.put(OIMClient.JAVA_NAMING_PROVIDER_URL, “t3://<OIM_HOSTNAME>:<OIM_PORT>”); System.out.println(“oimClient instance…”); oimClient = new OIMClient(oimClientEnvironmentVariable); System.out.println(“oimClientEnvironmentVariable : “+oimClientEnvironmentVariable); /* * Try Block Starts */ try{ /* * Establishes OIM Connection */ System.out.println(“Trying to Login to OIM…!!!”); oimClient.login(“xelsysadm”, “<XELSYADM_USER_PASSWORD>”.toCharArray()); System.out.println(“The Client Object is : “+oimClient); System.out.println(“OIM Login is Successful!!!”); }catch(Exception excOIM){ excOIM.printStackTrace(); } /* * Try and Catch Block Ends */ finally{ System.out.println(“****************getOIMClientConnectionUtilsMethod() Ends Starts*******************”); } return oimClient; } public void getUserAttributeDetails(){ UserManager usrManager = null; OIMClient oimClient = null; try{ oimClient = getOIMClientConnectionUtilsMethod(); usrManager = oimClient.getService(UserManager.class); }catch(Exception exc){ exc.getLocalizedMessage(); }finally{ usrManager = null; oimClient.logout(); } } } |
3) In the above code block, we have the following:
a) We have got the method named as: getOIMClientConnectionUtilsMethod() inside the Class :: oimClientConnection. This method is responsible for establishing the OIM Client connection and returning an object of Class: OIMClient.
b) In the other method named as: getUserAttributeDetails(), we call the method :: getOIMClientConnectionUtilsMethod() to establish the OIM Client connection. Once it’s called an object of Class: OIMClient is retrieved, then, instantiate the UserManager OIM API using the object of OIMClient class which is like below.
| UserManager usrManager = null;
OIMClient oimClient = null; oimClient = getOIMClientConnectionUtilsMethod(); usrManager = oimClient.getService(UserManager.class); |
4) Another way to identify on when to use OIM Client based connection while instantiating OIM APIs is:
a) When you develop any component which will be deployed inside the OIM server.
b) Refer to the table below for further details:
| Component Name of OIG | Where it is deployed? | Whether to use OIM Client based connection? |
| Standalone Utility | Outside OIM Server were its deployed as Jar | Yes |
| External UI/Web Application | Outside OIM Server were its deployed as Jar | Yes |
Conclusion
The choice between OIM Client and OIM Platform is contingent on the deployment location of your components. For components developed in Java or Groovy and deployed inside the OIM server, OIM Platform Class is your go-to for establishing a connection with the OIM Server. Conversely, for components deployed outside the OIM server, OIM Client Class is the appropriate choice. Understanding this distinction is crucial for optimizing your IAM solution and ensuring seamless integration within the OIG platform.
Author: Rohit Wekhande, IDMWORKS, Senior IAM Consultant