Think GRC is a complicated term and as nebulous as say, the Cloud? Well, think again! You may not have to go too far to understand what it is, as long as the context is clear. Let me simplify this for you.
GRC or Governance, Risk and Compliance, quite simply, represents your own nuclear family.
Comprising of a father, a mother and children, it is the umbrella term that denotes family. Just like the inherent cohesiveness within a family, it is incumbent upon and imperative for corporates to inculcate cohesiveness for implementing organizational Security and Governance.
Governance – This used to be your Daddy, but in a changed world with gender equity becoming the norm, it could be your Mommy as well. He or she lays out the rules (overall management approach) and expects that someone senior (deputed in their absence) enforces them (management processes). These are your professors, teachers and tutors. Your parents may leave home for work in the morning but the expectation is that you will do your homework, eat your veggies and turn in no later than 9 p.m. These are the rules of engagement.
Risk Management – This could be your mother’s role. She interprets Daddy’s governance, but chances are that there are quite a few chinks in the armor, which she needs to manage before he gets home, on a day to day basis. Most of them would have to do with the child’s indiscretions.
Risk – This is the teenager who could very well be a rebel without a cause and whom the mother needs to manage.
Compliance – These are the rules or stated requirements of the house, which one has to conform to. When you’re out of compliance, you will be held accountable by your parents, will have to fess up and mend your ways. At an organizational level, it is achieved through management processes which identify applicable requirements. At your home, the potential costs of non-compliance, for instance, are gauged against qualitative measures and projected expenses; and any corrective actions are taken into consideration. For example, your mobile bill just shot through the roof or your Internet downloads and streaming caused a hole in the family wallet. What’s the result? Severe curtailing of your privileges!
Just as the practical workings within a family are mostly qualitative in nature, so is the dearth of detailed scientific research on GRC today. The family, therefore, provides adequate context for the interplay between Security Governance, Risk Management and Compliance.
Enabling your Network Security controls with effective Governance, Risk & Compliance
It has always been about the business and not IT! That IT is a means toward achieving business objectives is as familiar as motherhood and apple pie. So also is the case with the role of Network Security Controls in achieving the Risk & Compliance objectives of your enterprise.
However, Network Security Controls seem to have lost their once dominant stature and place on the pedestal in the protection of today’s enterprise networks as the first line of defense. Increasingly, we see controls at the application layer being touted as that. Certainly, attack surfaces have changed and correspondingly, so have attack vectors.
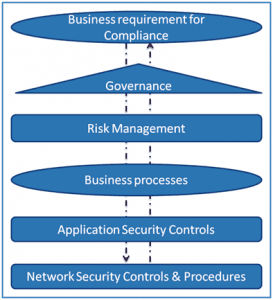
It is therefore essential to get the overall picture, and to utilize Governance, Risk & Compliance (GRC) to tie Network Security Controls with business requirements. We need answers for the following:
- Have application controls really taken up a new role?
- Do Network Security Controls still matter?
- What is the role of GRC?
- How does one bridge Identity & Access Management with the rest of the enterprise?
- How does one get the most out of one’s Identity & Access Management Controls?
Governance-driven risk management helps one make better informed decisions based on business impact, and provides a mature platform to design and implement controls at various layers. Business risk-aware security provides for more effective data protection, continuity and privacy, and in turn paves way for effective and sustainable compliance. Without security, privacy becomes a question, and without either of them, compliance is a mirage.
Knowledge about business processes, applications and data that are being protected will help strengthen the controls that are designed and implemented at the network infrastructure level. The IT general controls at the network level cannot afford to be treated as generic controls that are oblivious to the business requirements.
Strategies and tactics that aid this alignment are characterized by “always-on” or “connected” collaboration between IT and business stakeholders, and governed by Senior Management. The techniques and tools that facilitate this evolution are Governance, Risk & Compliance (GRC). In essence, Network Security Controls and GRC are tightly interlinked, and can be viewed from both a Top-Down or Bottoms-Up perspective. In the next update, we will dwell into the answers for the questions listed above.
Bonus Information: Saviynt is a leading Cloud Security and Identity Governance solution. Its modular platform improves efficiency, enhances your Security Posture, and helps you meet the business needs of today while preparing for tomorrow.