In the next frontier of digital engagement, Customer Identity Access Management (CIAM) emerges as a pivotal cornerstone for future-ready business strategies. As organizations gear up to offer unparalleled user experiences in this new era, mastering the nuances of CIAM becomes more crucial than ever. Over the wall. Drilling down. Synergize. Drill the ocean. What do […]
Part Two: IAM Assessment Blueprint Roadmap Your organization is aware that it needs Identity & Access Management. You realize the value of IAM Assessments and how they can help you identify and address the challenges your organization faces when properly implementing an IAM solution. However, the question may still remain, what should you do with […]
IAM Roadmap from Assessment to Blueprint and then Roadmap (ABR) is the path to a digital transformation for all CiSCO’s. Your organization cannot afford to assume that its IAM solution in its current state is providing the protection you need. IT departments and business leaders are facing increased scrutiny on how they protect access to […]
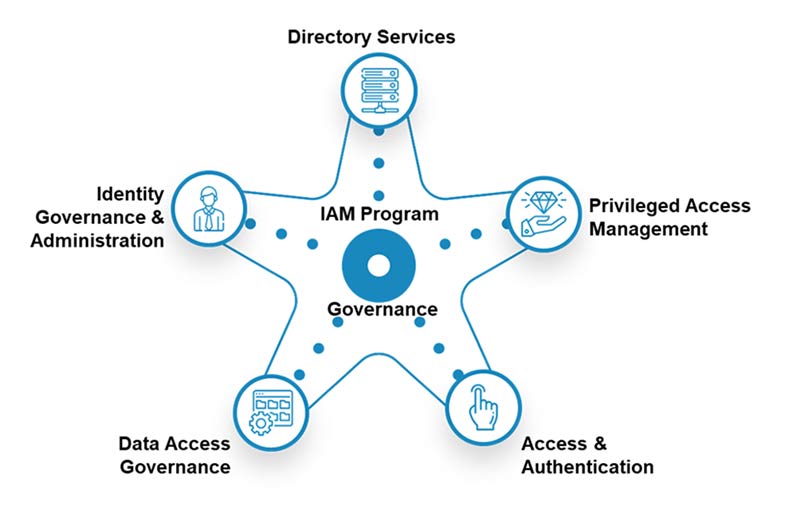
Customer Identity Access Management lets your company manage and capture customer ID and profile data. It lets you control how your customers access applications and services. A good CIAM solution will offer a variety of features, including: Self-service account management Preface and consent management Single sign-on Multifactor authentication Access management Data access governance Directory services […]
This guide highlights 11 pivotal questions that can steer you clear of potential pitfalls and towards a robust CIAM strategy for the future. In the intricate realm of digital identity management, ensuring a seamless and secure customer experience is paramount. As businesses navigate the complexities of Customer Identity Access Management CIAM, asking the right questions […]
How does a mature IAM program help limit the severity and scope of a hack? Like everyone else, I’ve been flooded with information about recent security events. There’s plenty of fluff circulating, but there is also some very good, thought-provoking discussions taking place. I recently read an article that discussed the idea of a “hack […]
Identity & Access Management has evolved to respond to changes to processes and technology. Behavioral analytics and zero trust have become integral components of identity management and access products. COVID-19 has forced organizations to have employees work from home. This has made it crucial to limit the access that remote employees, and partners and customers, […]
[vc_row][vc_column][vc_column_text] Tutorial for Identity Selector configuration for Role Owners Today’s blog features a tutorial detailing the Identity Selector configuration for Role Owners. We had a requirement to configure a Role Creation and Modification workflow for which there was a criterion defined for Role Owners. We have customized the Identity selector list for role owners in […]
ICYMI — Lil’ CISO has garnered a lot of attention with his PAM (privileged access management) song and video. So much so, that it’s spawned numerous requests to provide more information on the 12 steps outlined by Lil’ CISO for implementing a successful Privileged Access Management (PAM) strategy. In this blog, we will outline PAM […]
[vc_row][vc_column][vc_column_text] Problem We were working on a proof of concept and came across a scenario where Active Directory create user scenario was failing from IIQ 8.0+ with the following warning error: “Errors returned from IQService. An error occurred while setting a password for the account. The exception has been thrown by the target of an […]