Those of us that have been around the NetIQ / Novell community for a while, have had many wishes for iManager to be a better tool. Unfortunately the “one console to rule them all” was never the real intent of the product.
My recommendation is to use Apache Directory Studio (ADS) as a companion tool to iManager. It is free, easy to use, and can be installed on multiple platforms.
ADS provides five key features to help you get in, get out, and be productive.
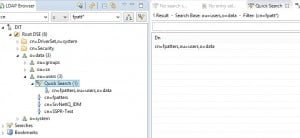
Quick Search
After you install and login for the first time, if you go to the container you are wanting to start your search from, you can highlight that OU and enter an attribute you want to search on and the string of the value.
Searches
Searches is a functionality that is quick and easy. iManager has some functionality but nothing like ADS. On the left you will have a Searches item. Searches allows you to create your own custom searches that will remain ready to be ran. You can use complex searches and have it return whichever data you would like.
An example may be that you want to quickly find all users that haven’t logged in for a period of time. You can specify to return the employee type, the employee status, their password expiration time, if their account is disabled, and when they last logged in. This is one example that would give you a quick view of users.
With an existing search you can right click on the search and choose export and export the results to an LDIF file.
Batch Operations
Have you needed to modify a lot of users at the same time with the same data? iManager can do this, but you’d have a lot of clicking to do.
Using ADS instead you could create a search setup that has all users that currently have an employee type of contractor, and an employee status of terminated, and have an account disabled. You can right click on that search and choose new > new batch operation > confirm the ldap search settings are correct > choose next and then choose the delete operation. It will delete all users associated with that search criteria.
You can also modify entries and execute LDIF change types on the objects returned from the search. With modify, you can choose to add, replace, or delete given attributes and values of the users. With the executing of LDIF change types, you can choose to to perform the operation and just generate the LDIF you need to use and save the LDIF out.
Copy existing values
Have you ever needed to copy content from one object to another? I needed to create rights in various locations for a user with different property rights. This is quite cumbersome in iManager. A lot of clicking and finding the property.
With ADS you can do this quickly:
- Find the user and on the right side, highlight the attributes and values you want to copy.
- Use the shift click to get them all.
- Right click on the selected values and choose copy values.
- Then go to the object you need the values and right click in the right frame of the user, where the similar attributes are, and choose paste.
If you don’t have all the values exactly correct, but they are similar, it still saves you a lot of time as you can then make the modifications you need.
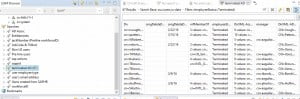
View Search Data
After your search is composed, you can click on the search item and refresh it. In the right frame you have the results that you can scroll through with the returned attributes in columns. You can then sort the returned values.
So if you have a field generated with the YYYYMMDD dated format for when a user is disabled, terminated, created, etc; you can easily sort and view the user’s various phases.
Another nice feature is that you can click on the copy table icon and then paste it into a spreadsheet.
Reports just got a lot easier.
These are just a few of the features with ADS. It gets the job done quickly. The free tool provides all of the mentioned functionality above. It will turn to be your “Go to tool” and iManager will become your companion tool for specific operations.
Note: iManager has many plugins that are needed and must be used for certain tasks. Do not assume that all operations performed in iManager can be replaced.