How does a mature IAM program help limit the severity and scope of a hack?
Like everyone else, I’ve been flooded with information about recent security events. There’s plenty of fluff circulating, but there is also some very good, thought-provoking discussions taking place. I recently read an article that discussed the idea of a “hack scale”. This article used a five-stage model for determining the severity of a hack or breach incident. The Cliff’s Notes version is this:
- Stage 0: The attackers have found or made an entry point to systems or the network but haven’t used it or took no action.
- Stage I: Attackers have control of a system but haven’t moved beyond the system to the broader network.
- Stage II: Attackers have moved to the broader network and are in “read-only” mode meaning they can read and steal data but not alter it.
- Stage III: Attackers have moved to the broader network and have “write” access to the network meaning they can alter data as well as read and steal it.
- Stage IV: Attackers have administrative control of the broader network meaning they can create accounts and new means of entry to the network as well as alter, read, and steal data.
This approach strongly resonated with me. I immediately thought about how this scale could be used to communicate the ways mature Identity & Access Management processes and technology implementations can help prevent these negative events and to slow the progression of a bad actor if they do get access.
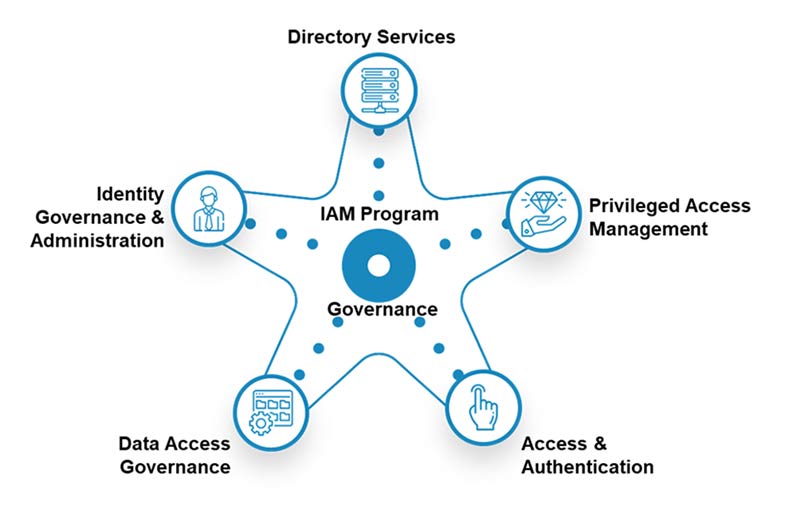
At IDMWORKS we talk about the six areas of Identity & Access Management that can be found on our starfish:
- IAM Program Governance: – It all starts here. Align the IAM Program with the Security Program and the Business Goals. Ensure policies are clear. Align Standards to frameworks such as the NIST Cybersecurity Framework. Create an IAM guidance group made up of IT leaders, Security leaders, and business leaders to set priorities and drive activities.
- Identity Governance & Administration (IGA): Timely access grants and removals. Account and entitlement reviews to ensure proper access. Enforce Separation of Duties policies.
- Directory Services: Strong password policies by account type. Auditing and monitoring for suspicious activity. Data standardization to aid forensic investigation.
- Privileged Access Management (PAM): Just-In-Time Access for privileged access. Privileged Session Management. Application to application privileged management.
- Access & Authentication: Implement MFA everywhere – seriously, do this. Passwordless authentication. Secure Web Gateways and Cloud Access Security Brokers.
- Data Access Governance: Protect the unstructured data in your organization! Data Classification. Data Access Reporting. Data Access Certification.
There is so much more to the story than what we’ve outlined above. Do you want to know more? Do you want to learn where your organization is mature and rising to the occasion and where there is an opportunity to improve? IDMWORKS is here to help.